Welcome to Constant Etherpad!
These pads are archived each night (around 4AM CET) @
http://etherdump.constantvzw.org/
An RSS feed from the etherdump also appears on
http://constantvzw.org/
To prevent your public pad from appearing in the archive and RSS feed, put or just leave the following (including the surrounding double underscores) anywhere in the text of your pad:
__NOPUBLISH__
Changes will be reflected after the next update at 4AM.
% METHOD: FMEM and /DEV/MEM
% WHAT: Different ways of exploring your memory (RAM). Because in unix everything is a file, you can access your memory as if it were a file.
% WHEN:
% WHO:
% URGENCY: To try and observe the operational level of software, getting closer to the workings, the instruction-being of an executable/executing file, the way it is when it is loaded into memory
rather than when it sits in the harddisk
% REMEMBER: In Unix-like operating systems, a device file or special file is an interface for a device driver that appears in a file system as if it were an ordinary file. In the early days you could fully access your memory via the memory device (/dev/mem) but over time the access was more and more restricted in order to avoid malicious processes to directly access the kernel memory. The kernel option CONFIG_STRICT_DEVMEM was introduced in kernel version 2.6 and upper (2.6.36–2.6.39, 3.0–3.8, 3.8+HEAD). So you'll need to use the Linux kernel module fmem: this module creates /dev/fmem device, that can be used for accessing physical memory without the limits of /dev/mem (1MB/1GB, depending on distribution).
% HOW:
% INCLUDE:
http://observatory.constantvzw.org/etherdump/files.md
511-535
Besides opening the memory dump with an hex editor you can also try and explore it with other tools or devices. You can open it as a raw image, you can play it as a sound or perhaps send it directly to your frame-buffer device (/dev/fb0).
% WARNING: Although your memory may look like/sound like/read like gibberish, it may contain sensitive information about you and your computer!
% EXAMPLE:
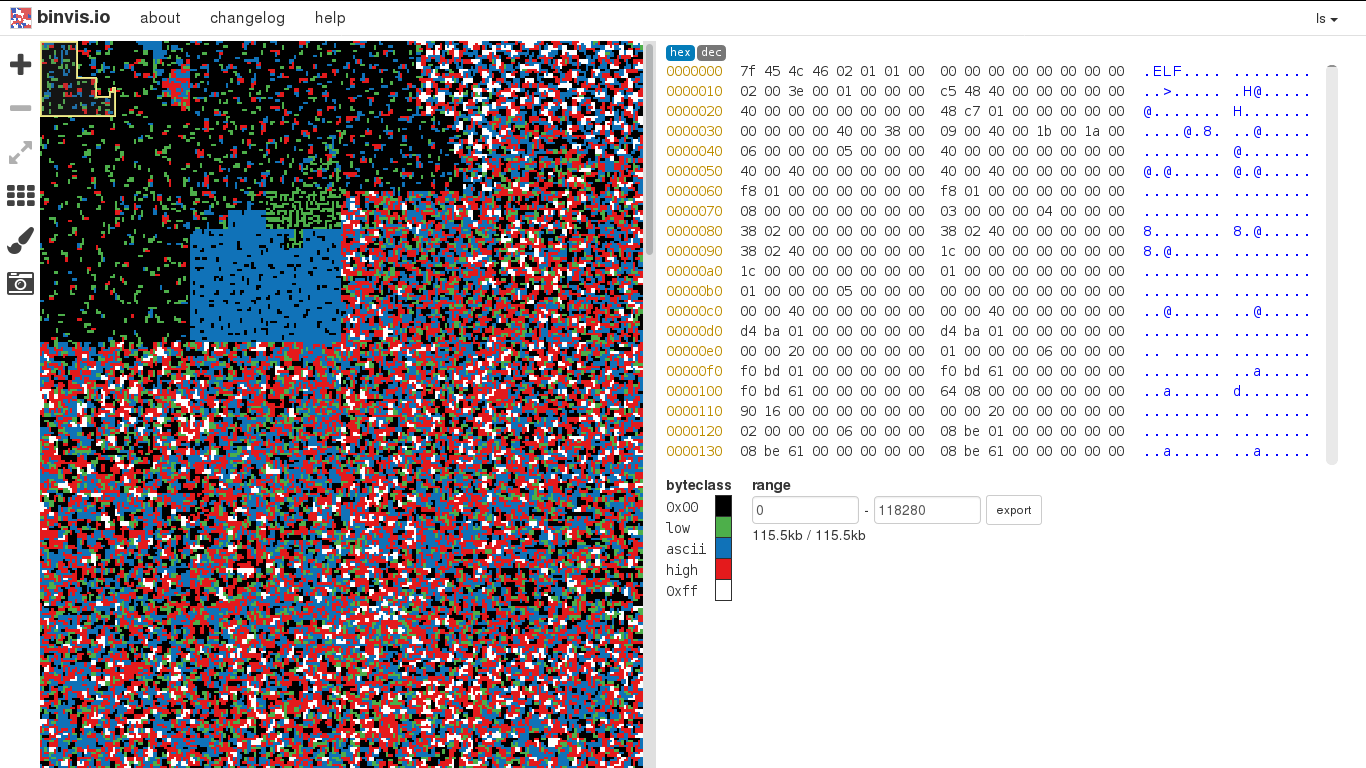
% BOX: Forensic and debuggung tools can be used to explore and problematize the layers of abstraction of computing.
% SEEALSO:
http://pad.constantvzw.org/p/observatory.guide.monopsychism
% SOURCE:
http://observatory.constantvzw.org/etherdump/files.html